Any breach in the security system can pose a devastating impact on your services, product, or organization as a whole. So, whether you are dealing with a highly secure collaboration solution, or working on a secure video conferencing solution development, be it a VoIP solution, or a WebRTC app development, if any anonymous person intrudes into your system then it might cost heavy on your pockets.
But, if there lays this problem then there must be some solution about it, among the plethora of ways out there to tackle the menace of hacking and privacy concerns, one of the modern & dynamic technology is the Honeypot. It may seem to be new terminology to you, but has been prevailing in the cyber arena for decades!
In the coming sections, we will discuss and know the challenges, advantages, disadvantages, and applications of Honeypot and get familiar with the terminologies related to it.
Honeypots… Introduction
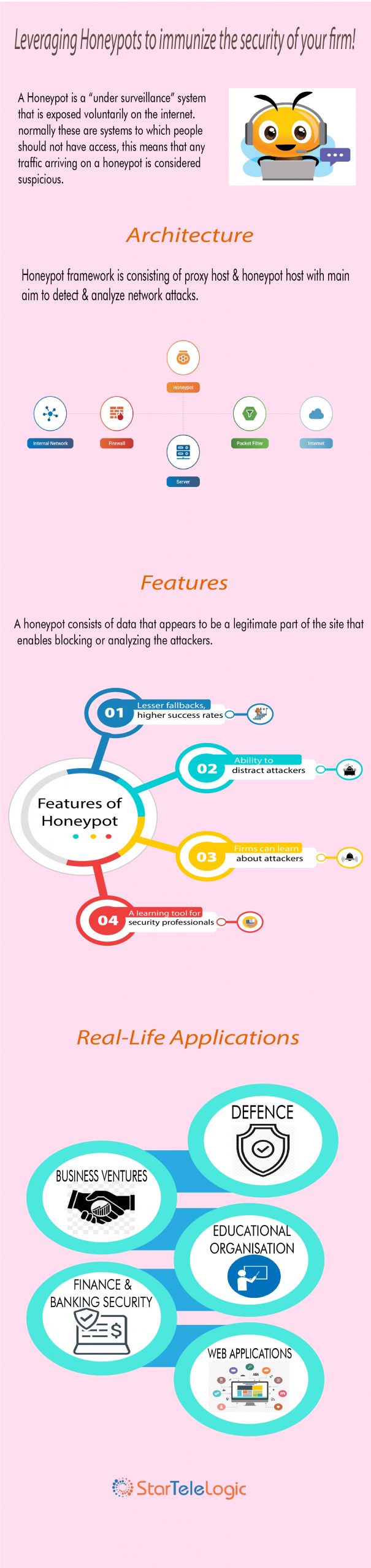
There could lay many definitions revolving around Honeypots, and it’s a bit tedious to define a honeypot due to its dynamic nature. It involves various verticals of security such as prevention, detection, and information gathering. But we have come across a generalized definition of Honeypots that says:
“A honeypot is security bait, in which attackers can easily be trapped to and then can be probed, or tracked.”
Therefore, Honeypots serve several purposes such as:
-
It can distract attackers from a more valuable machine such as a server or any repository over a network.
-
Can provide a precaution about any new attack or exploitation trend; and
-
Provide an in-depth examination can be done in the course of or after the exploitation of a honeypot.
Hence, we can say that, like cheese-baited mousetraps pull mice towards it, in a similar way, attackers are attracted to honeypots. They think it to be a legitimate target that is worthy of their time & effort.
So, the intruder interacting with the Honeypot is by its definition, unauthorized.
There is another term that comes into picture when we speak of Honeypots; it is Honeynet, which can be defined as a “network of honeypots“.
Now, as we are clear about the basic terminology of Honeypots, let’s further discuss various types of Honeypots.
Honeypots… Classification
Honeypots can be classified under two broader categories: Based on their purpose (such as production, research, and honeytokens) and level of interaction (low, medium, and high). Each of these two types is further elaborated as:
-
Purpose based Honeypots
Research Honeypot
-
It gains information about the blackhat community and does not add any direct value to an organization.
-
They gather information based on general threats faced by the organizations which allow organizations to protect themselves against those threats.
-
The primary motive of research honeypots is to study the lines of attack followed by attackers. It is very similar to the research analogy followed by startelelogic to understand the motives, behavior, and organization of the attackers.
-
These are very complex to deploy and maintain and can be very time extensive.
Production Honeypot
-
It is used within an organization to protect and mitigate the risk.
-
It provides immediate security to a site’s production resources.
-
It requires less functionality then research honeypot, it is easier to build and deploy.
-
It identifies the attack pattern but it gives less information about the attackers as compared to the research honeypots.
-
It invites attackers to interact with the network or system by doing the mirroring of the production network of the company.
-
Honeypots based on the level of interaction
Low-interaction Honeypots
-
It accesses the services that cannot be breached easily to provide total access to the honeypot.
-
There is no interaction of the operating system to interact with.
-
Deployment & maintenance is easy.
-
An example of the commercial low-interaction honeypot is honeyed.
Medium-interaction Honeypots
-
In terms of complexity, it lies between low-interaction honeypots and high-interaction honeypots.
-
It also does not have an operating system installed but the simulated services are technically more complex.
-
It provides a better illusion of an operating system to the attacker.
-
Examples include mwcollect, nepenthes, and honeytrap.
High-interaction honeypots
-
It is the most advanced honeypot.
-
These are the most complex and time-consuming to design.
-
It involves the highest amount of risk because the actual operating system is involved.
-
The goal of a high-interaction honeypot is to provide the attacker with a real operating system to interact with; in this case, nothing is simulated or restricted.
-
An example includes a Honeynet that is used for research purposes.
Honeypots… Advantages & Disadvantages
“Knowledge is Power“, this quote holds for both; security practitioner, and the person who breaches the security. Having know-how about both advantages and disadvantages of honeypots is a must.
Advantages associated with Honeypots
-
Handy Data Sets: The main focus of Honeypots is the traffic that comes to them. Although they do not have huge data logs or the data set may be small, but the information gathered is of high value.
-
Meager Resources: A low-end system can be used as a honeypot as they only capture the bad activity, so the requirement of resources is minimal.
-
Flexibility: Honeypots are very simple to develop, they do not involve any complex algorithms, state tables, or signatures to update and maintain.
From these advantages, we can see how honeypots can add value and enhance the overall security of your organization.
Disadvantages associated with Honeypots
-
Short-sighted: The activities of the attacker are tracked and captured by a honeypot only when they interact with them. While the other parts of the system remain untraced. Hence, for you, it becomes of utmost importance to build a highly secure network similar to the one developed by our experts.
-
Fingerprinting & Discovery: Fingerprinting means when the deployed honeypot is identified by the attacker. It happens because honeypot has certain characteristics or behaviors, and even a simple mistake can act as a signature for a honeypot.
-
Risk of Taking over: There is also a risk of the takeover as if taken over by attacker; it can be misused for systems within or outside the organization.
Honeypots… Applications
Here we will discuss the implementation of Honeypots in various areas such as the internet, with IDS and its application.
Honeypot with IDS
IDS or Intrusion Detection System discriminates between the incoming traffic from various clients and attackers respectively. By doing so, it eases the issues related to throughput, latency, and the security of the network.
Honeypot in Internet
Honeypot measures the actual attacks that take place on the Internet. A honeypot can take the form of some services, an entire OS, or even an entire network, but in actual it is a tightly scaled compartment that is built to attract attackers.
Role of “Hybrid Honeypot” in Network Security
Deployment of low-level interaction honeypot and high-level interaction honeypot comes under the umbrella term of Hybrid Honeypot.
Hence to offer an extensible infrastructure for the installation of honeypots, and scaling up of detection mechanisms features of both the honeypots are needed to be combined.
Honeypots… Endnote & Future Outlook
Hence, we have provided a brief overview of what Honeypots are; their classification, advantages, disadvantages, and applications.
As we have begun with the importance of internal security systems, the security experts at startelelogic maintain the security stack associated with applications and conduct research on new and organic threats. We continuously update our security policies, identify vulnerabilities and threats in our software development life cycle itself, and then customize rules as per your needs.
Well, instead of going for traditional honeypots, our team leverages learning the stuff from attacks witnessed across various domains in this vertical. startelelogic’s applications and solutions are nothing but a combination of multi-layered security protocols based on these research and findings over the period.
Honeypots are becoming increasingly popular, although being a new technology, it has found many commercial applications that are easy to use and administer. You can learn more about startelelogic’s flagship products such as Trillup and Telemo which are highly secured audio, video, cloud telephony services, and contact center solutions. Further, as honeypots can be used to gather information on attackers and other threats, we believe they can prove to be a useful tool in the coming digital era. Therefore, if you also want to leverage this fast-paced, growing, and secure technology or want to update your application, or network by implementing it, then get in touch with our experts to stand out in securing your organization’s network both; from internal as well external security threats.